In the spring of 2018, cybercriminals attacked a multi-specialty practice, a lab-testing company and an electronic health records developer in just a few weeks. In the most alarming example, they infected a Missouri clinic with multiple types of malware. Then, as the hackers made their exit, they also infected the clinic with ransomware to cover their tracks.
The diagnosis is clear: Healthcare is under attack from hackers, and no one is exempt or immune. The cost of a data breach is also rising, with each record lost now costing healthcare organizations $ 408, compared with $ 380 a year ago. Even worse, healthcare faces a higher cybersecurity liability than any other industry—nearly three times higher than the average for all other industries ($ 158).
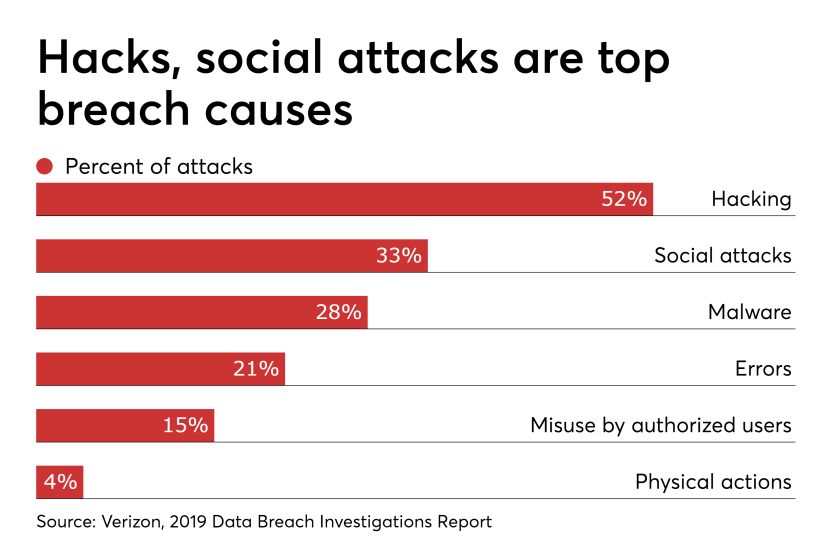
Hackers target the healthcare industry because even the smallest providers have valuable data, even though they often do not have strong cyber protections in place. In yet another example, hackers gained access to the consumer portal for Humana health insurance. The damage could have been limited if someone had noticed and acted quickly. Instead, the problem went unnoticed for almost four months, during which time hackers stole names, addresses, policy information and partial Social Security numbers. Unfortunately, this kind of slow response is all too common.
Why speed matters in cybersecurity
So how could large-scale theft go unnoticed for so long? Compared with physical theft, cybercrime does not set off alarms or show up on security cameras. And unlike financial crimes, stealing data does not show up on the account ledger. Hackers can siphon off huge amounts of data in secret when proper mechanisms aren’t in place to monitor the problem.
To put that problem into perspective, consider that 58 percent of all email traffic at healthcare organizations is malicious or unauthorized. Malicious emails contain malware, ransomware or other cyber infections. Unauthorized emails contain sensitive information that is not authorized to be sent or received. Any of these types of emails can compromise cybersecurity, put data at risk, or breach compliance rules. Considering that these risky emails constitute the majority of email traffic for healthcare organizations, the problem obviously isn’t being properly addressed.
Part of why response times are so slow is that threats are so well-disguised. Business email compromise schemes, for example, use personal information and familiar details to persuade recipients to hand over information, such as login credentials or account details. The deception is so subtle that someone can commit a major cybersecurity mistake without realizing there is any problem at all.
Humana is hardly the only organization to go months without noticing an attack. And now that hackers are using ransomware to create smoke screens around their escape routes, limiting the damage from attacks will become harder than ever. Avoiding attacks altogether is still the best option.
3 keys to protecting patient information
A proactive approach to cybersecurity helps you deflect more threats—and detect them faster. An effective protection plan includes:
- Multiple layers of security: No single layer of cyber protection is adequate. Healthcare organizations should rely on multiple layers of security that ensure a robust, effective defense on all fronts. Strong security includes technical and nontechnical solutions, such as enterprisewide policies and a culture that prioritizes good data governance.
- Extensive employee training: Because most attacks originate in the email inbox, individual users are often the first point of contact. Educate users on the importance of cybersecurity in healthcare, and then further train them how to identify and avoid the most common threats. As so many attacks try to catch people off-guard, cautious users present a formidable defense.
- A focused cybersecurity strategy: Place a greater focus on the weakest link: the email inbox. Most attacks begin in an inbox because emails can easily bypass cyber defenses and just as easily trick recipients. Making the inbox a priority ensures that limited cybersecurity resources are directed where needed the most.
The fundamental priority of all healthcare organizations is to provide exceptional patient care. While protecting sensitive patient data is not always immediately recognized as a top priority, data protection is closely related to overall patient care. If healthcare organizations of all sizes want to fulfill their missions, cybersecurity clearly needs to be a top priority moving forward.
